RevBits PAM – Full coverage and easy delivery at enterprise scale.
An access management solution that offers multiple access control modules in a single solution to manage privileged user accounts across the organization.
Features
Native Clients - As a result of an extensive reverse engineering effort, RevBits Privileged Accessed Management (PAM) uniquely provides native clients on all operating systems for all supported protocols. This means that privileged users are free to use any tool to connect to their assets while being fully protected by RevBits PAM and maintaining the full functionality of the original protocol. Native clients are available for SSH, RDP, VNC, Telnet, Oracle, MS SQL, PostgreSQL, MySQL, Cassandra…
Web Application Monitoring – As businesses increasingly rely on web-based applications (SaaS), RevBits PAM supports onboarding and monitoring of any application and HTTP sessions.
Extensive monitoring and logging - All privileged sessions can be recorded both on video and with keystrokes. All recording is done strictly on a central server to prevent tampering with evidence. Exclusive to RevBits PAM and powered by our native clients, all database activity can be logged at the individual SQL statement level. Command watchlists and filtering are available, while clickable keylogs make navigating to relevant video segments extremely easy.
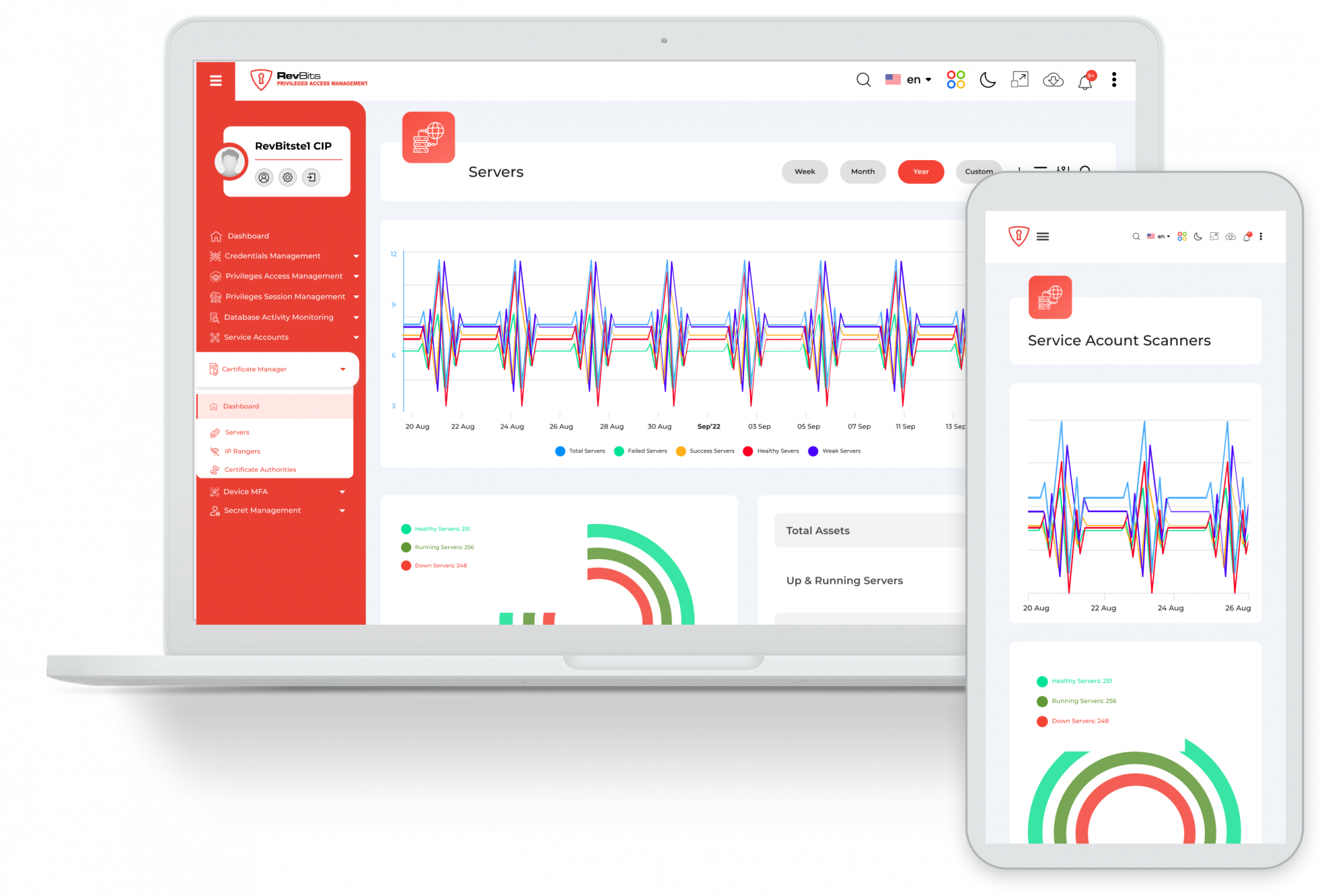
Extensive reporting and analysis – A large set of audit reports and metrics are available as standard features. Customized detailed reporting and analysis is provided through an easy-to-use, dynamic query language that allows even non-technical users to generate sophisticated reports.
Behavioral Analysis – RevBits PAM will gradually learn the usage pattern of privileged accounts and proactively alert if anomalies are detected.
Integrated Workflow Management – An integrated workflow engine and visual designer make it easy to create even the most complex multi-level approval workflows for granting access to assets. For auditing purposes, all workflow execution steps are recorded and stored.
Automated Cloud Asset Onboarding – Automated asset discovery and onboarding for all major cloud infrastructure providers.
Management
Automated Data Migration and Asset Onboarding from Existing PAM Solutions – To meet customer requirements for automated data migration and asset onboarding from popular PAM solutions, RevBits PAM developed technology to enable administrators to perform migration efforts of the system quickly and cost-effectively.
Monitoring and recording - Using native clients, Privileged Session Management provides monitoring and recording of assets that are not integrated into PAM. Sessions can be taped and video recorded.
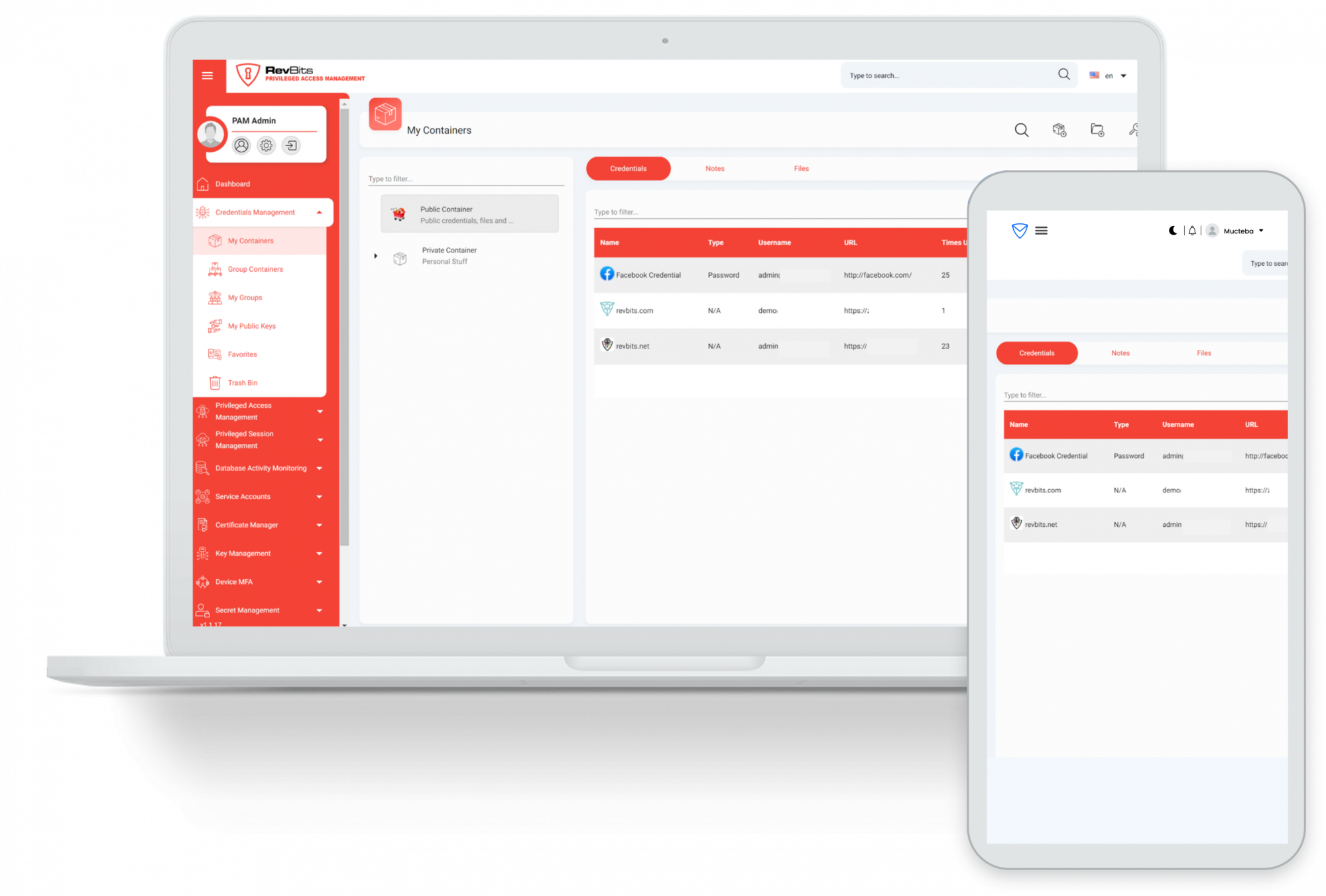
Customizable Password Management – The password management module supports authentication to common protocols such as web applications, SSH/RDP/VNC servers, and more.
Hardware Tokens - Extend authentication security with hardware security modules (HSM), smart cards, USB tokens, near field communications (NFC), and RFID technologies.
Complete platform coverage – Native apps and browser plugins are available for all major platforms and operating systems. Operating systems include Windows, Linux, Mac OS, iOS, Android (OS) and browsers include Chrome, Firefox, Opera, Safari, IE and Edge.
Stop acquiring data into memory - The password manager will block unauthorized access to process memory.
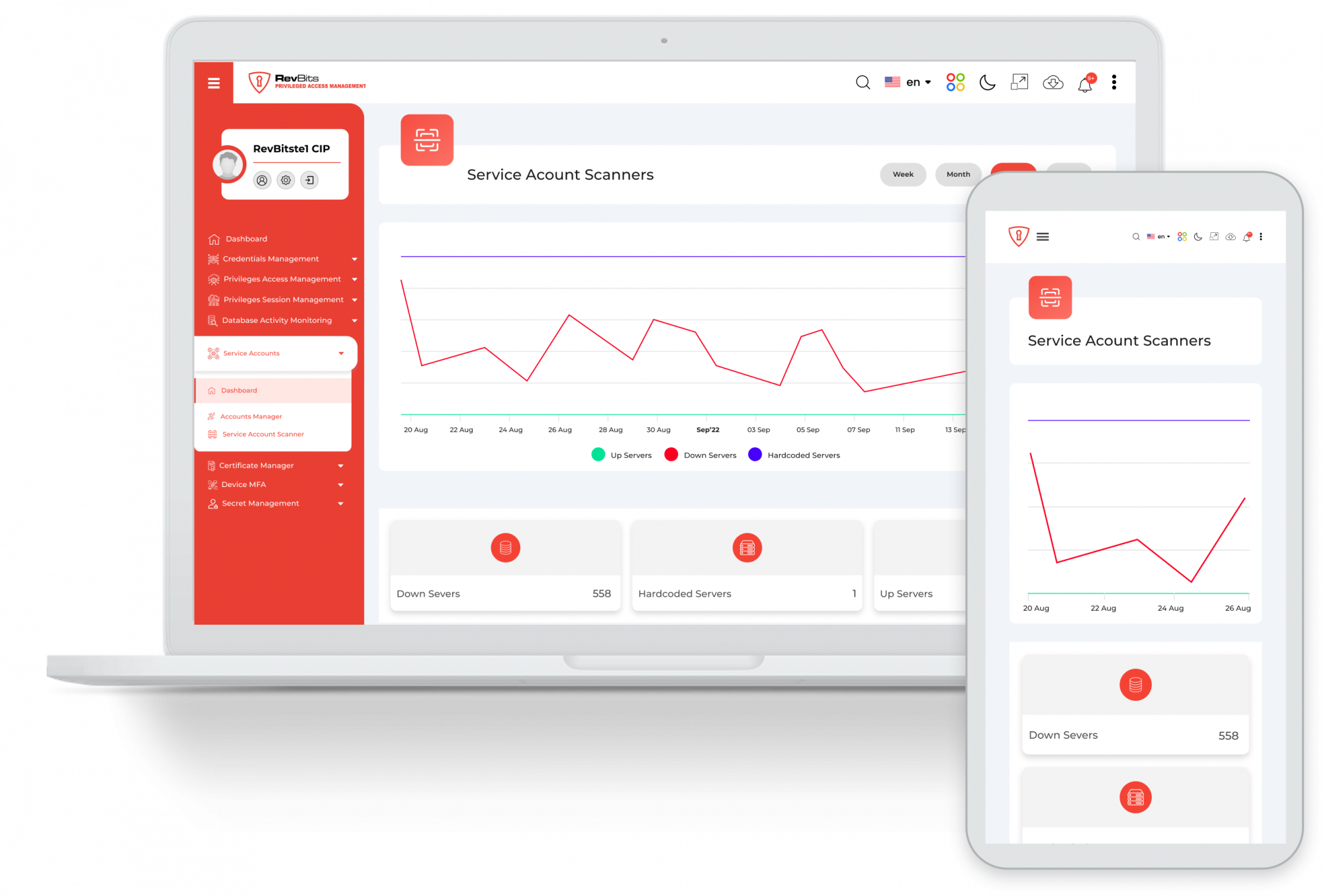
Service Account Management – The module can scan and onboard service accounts, scheduled tasks, and IIS web applications running in the context of encrypted credentials.
Run services under managed control - Run selected services, applications, and scheduled tasks in the context of a managed service account.
Proper security for services - Through the module, secure service account passwords with automatic rotation and proper maintenance.
Integration
Common Pipeline Toolset Integration – The RevBits CI/CD module enables seamless integration with the most popular CI/CD pipeline toolsets. The module supports Jenkins, Puppet, Terraform, OpenShift, Ansible, Docker, Cloud Foundry, and Kubernetes with future tools in development.
Secure Secret Management – Installing the RevBits CI/CD pipeline plugin into your existing secure secret management solution throughout the CI/CD lifecycle enables easy management of users, credentials, and assets. CI/CD.
Certificates
Multi-Factor Authentication – Configurable to require the use of multi-factor authentication for users to access network assets.
Protective SSL Scanner - SSL Scanner provides regular updates on expiring certificates, identifies weak hashing algorithms (in certificates) and other weaknesses in SSL implementations.
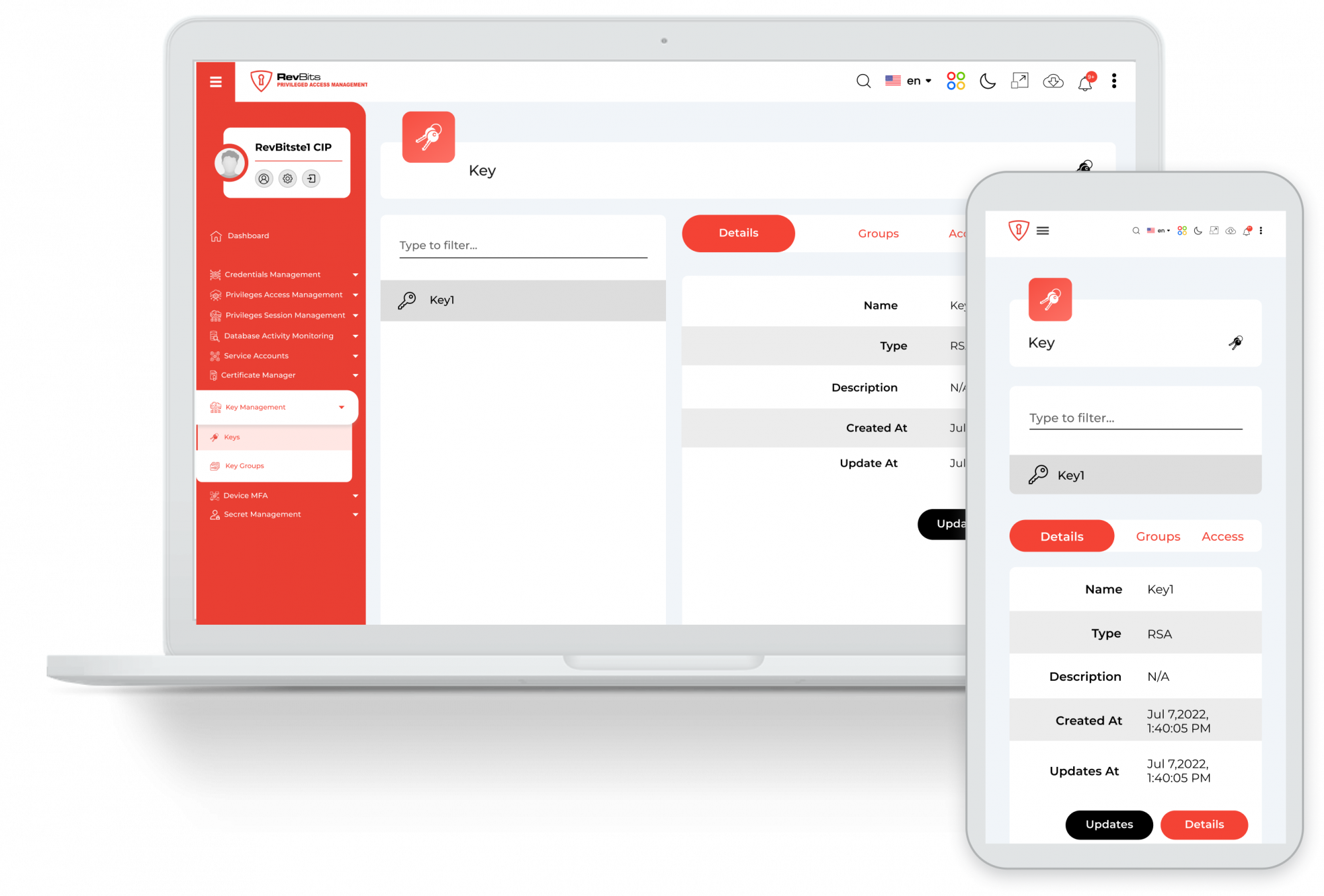
Key Management - Complete key management Generate symmetric and asymmetric keys and encrypt, decrypt, sign and verify data, all in one module with complete source code examples
Guaranteed data security - All data is encrypted and decrypted in the browser, never on the server; ensures that if the server is breached, only encrypted data can be accessed. The keys never leave the device. (US Patent)
Comprehensive Dashboard – RevBits Privileged Access Management Dashboard provides administrators with a complete overview of the status of passwords, privileged sessions, keys, and certificates.