Access all integrated solutions with a single click
Access to any contracted RevBits product is easy and just a click away.
RevBits Endpoint Security (EPS)
RevBits EPS's unique architecture has custom drivers or proprietary application load detection capabilities, which find malicious activities at various stages that attempt to impersonate Windows applications, signing processes, and trusted processes. RevBits EPS also has an accurate detection engine that prevents false positives and a distinctive architectural design for application whitelisting, sandboxing, spawning, and parent/child process analysis.
Read more
RevBits Email Security
It is a native solution provided by SaaS, also known as Integrated Cloud Email Security (ICES). The Endpoint-based agent protects against malicious emails by taking over a secure email gateway. Fill security gaps by leveraging distributed processing for deep scanning across remote user endpoints to detect and block malicious emails that bypass the centralized layer of an organization's security stack.
Read moreRevBits Deception Technology
By deploying honeypots based on real servers in a dual virtualization environment, malicious actions from external or internal threats are immediately detected and reported. RevBits Deception Technology (DT) uses the most common database servers, file sharing services and more.
Read more
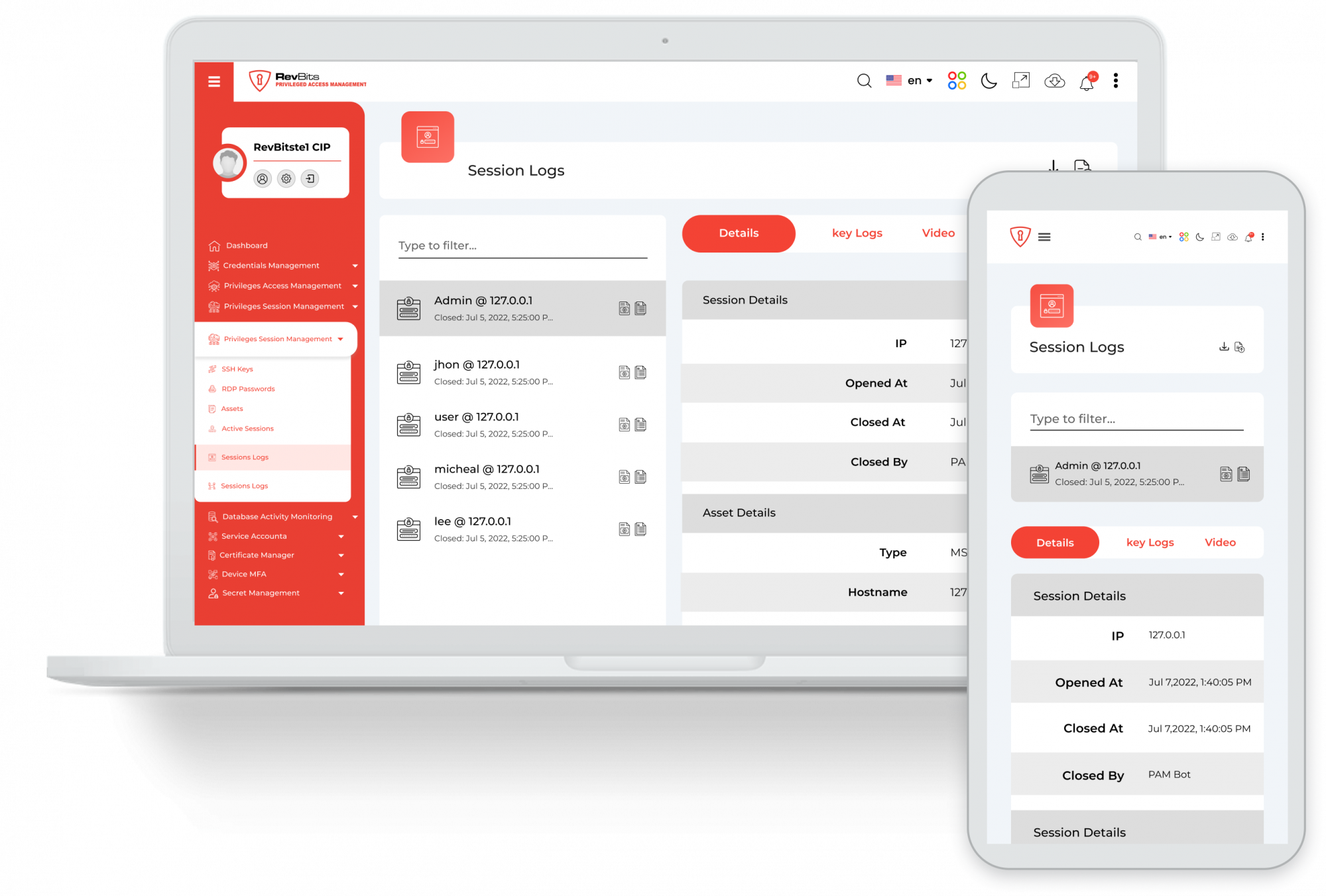
Privileged Access Management
RevBits PAM is an advanced access management solution that includes six modules and extensive session logging that captures keystrokes and video. RevBits PAM has two US patents: browser-based zero-knowledge encryption and authentication authority that extends to various hardware security solutions. These unique access control capabilities reduce supplier relationship management efforts and increase access management protections.
Read moreZero Trust Networking (ZTN)
RevBits ZTN's auto-scaling capability and keypoint geolocation distribution make RevBits ZTN the fastest ero trusted network on the market. Deep assessment of an Endpoint's security posture inspects tunnel traffic for malicious content and data security. RevBits ZTN creates a logical access boundary based on identity and context that spans users and their applications. Applications are hidden and access is restricted using a trusted agent with a collection of named entities. The broker verifies the identity, context, and policy compliance of the specified participants before allowing access.
Read more