Deception technology
As malicious actors have become more sophisticated, the need for intelligent security has increased.
Features
Robust Monitoring – RevBits deception technology provides insights into current attacks to detect, track and respond to sophisticated threats in real time.
Fortified Jail – The decoy's dual-layer virtualization ensures it is nearly impossible for malicious actors to escape.
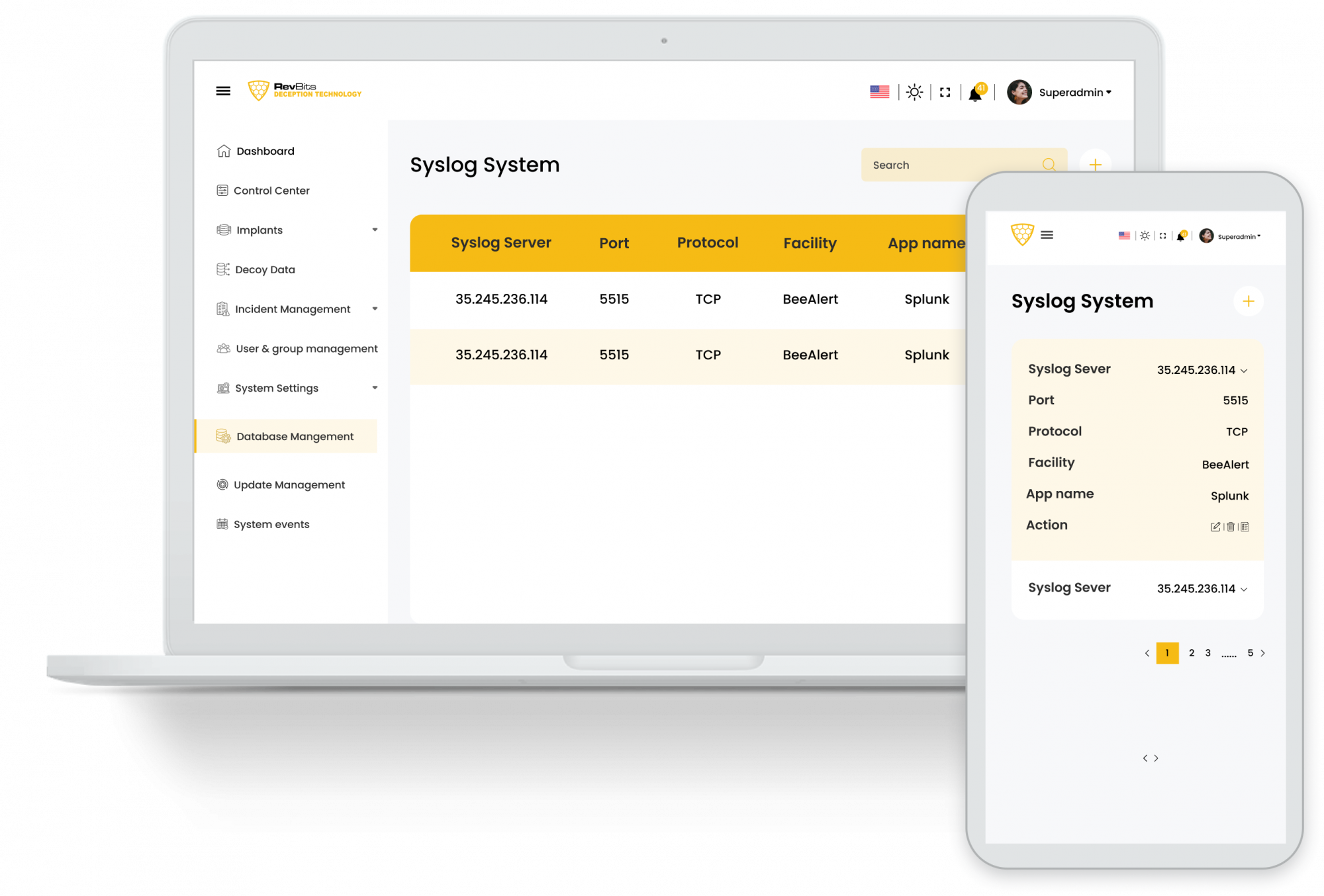
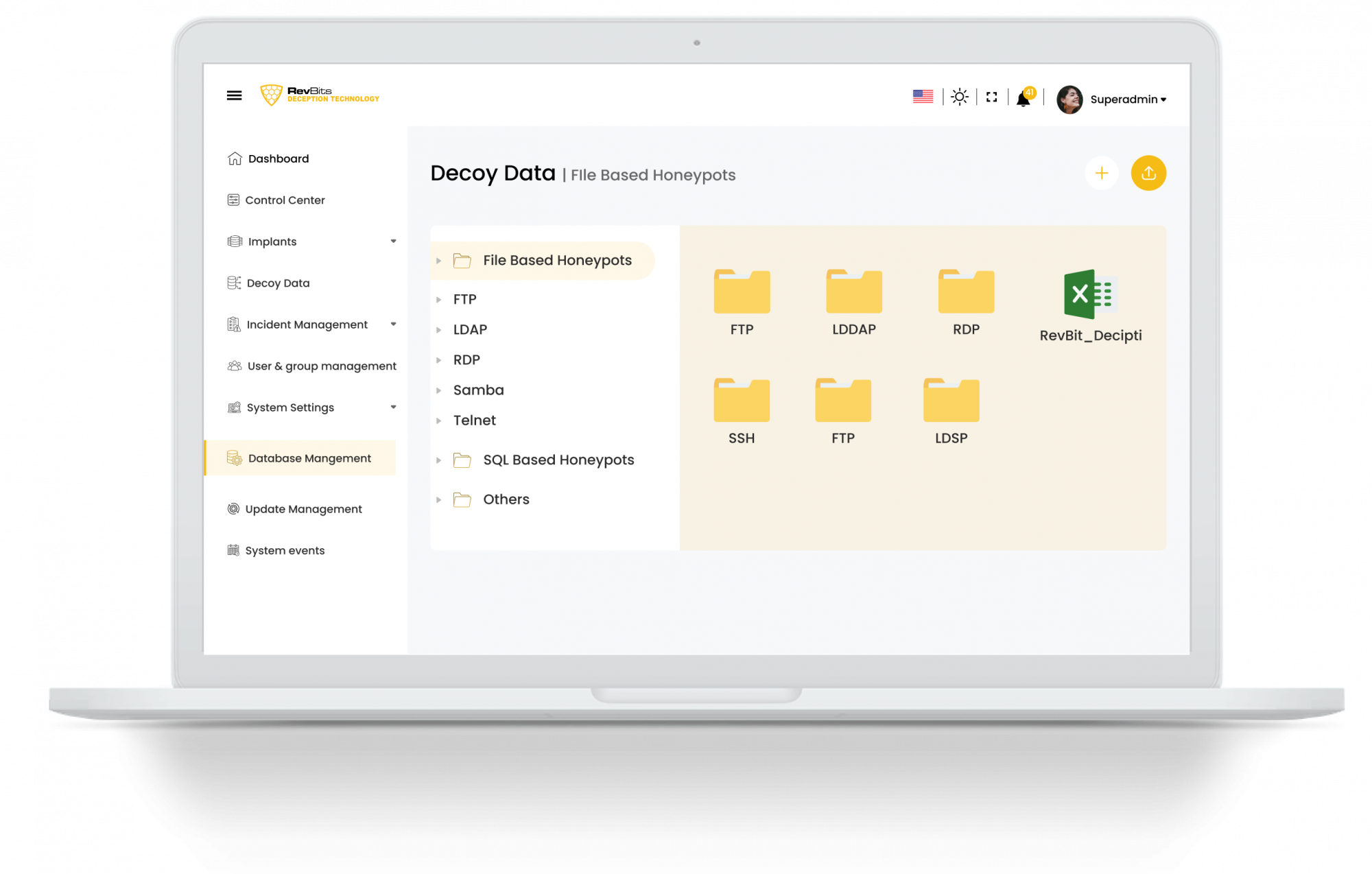
Deploy popular servers and applications - RevBits cheat technology uses the most common database servers, file sharing services and many others.
Cloud Ready - Cloud images available for Amazon, Google and Azure for use with deception technology implemented.
Attractive Bait – RevBits deception technology leverages two methods to implant attractive baits. System administrators have the option of manually deploying breadcrumbs into application configuration files or automatically deploying credentials (honey drops) to network workstations. Both breadcrumbs and honey drops will lead attackers to the decoys and reveal their source.
Simple and Fast Deployment – Install RevBits deception technology on any server within the network.
Low resource consumption - Numerous decoys can be launched within each MV, minimizing system resources and maximizing operational efficiency.
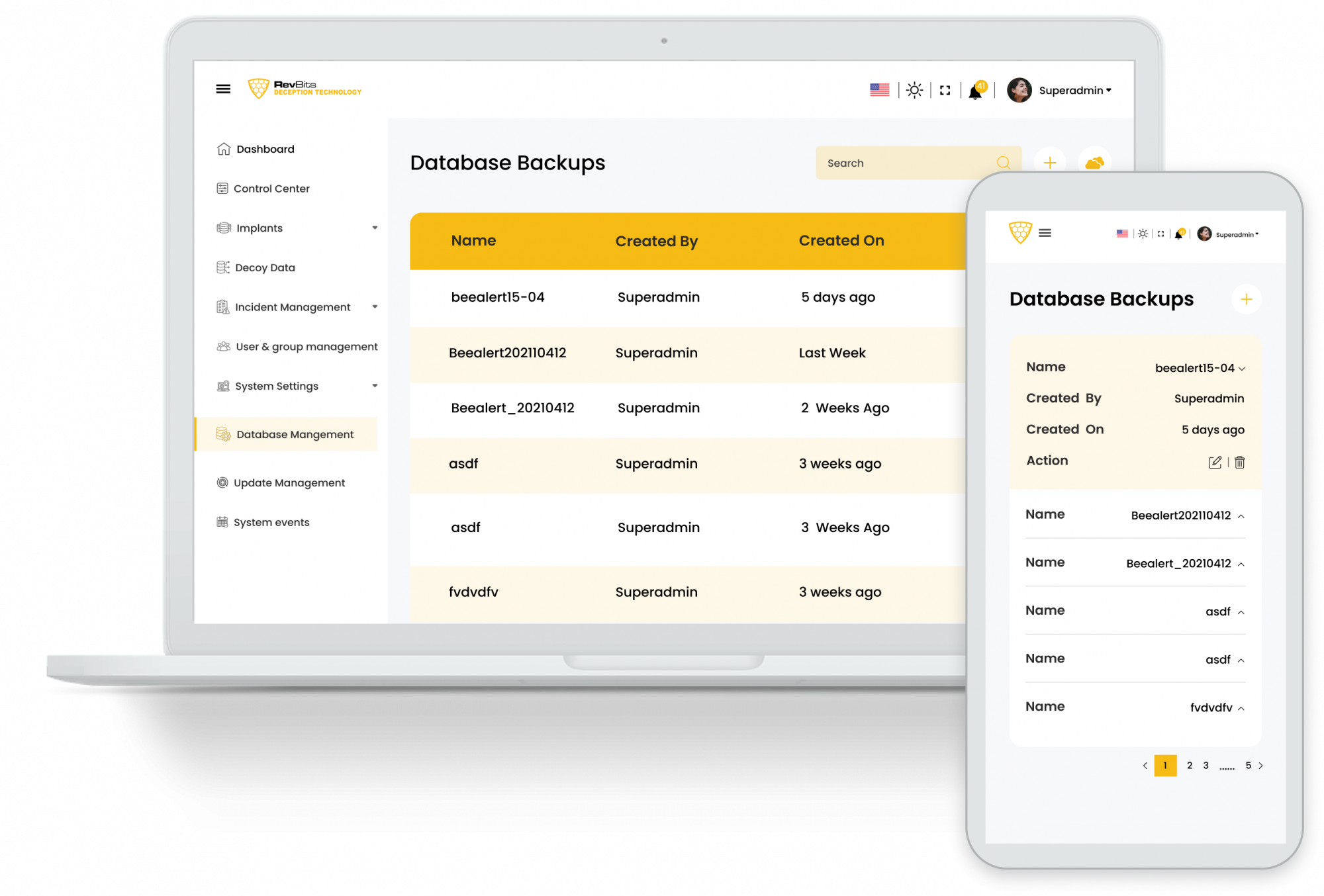
Immediate Image Access – RevBits maintains all decoy images and automatically pulls and deploys them to the client's network on demand.
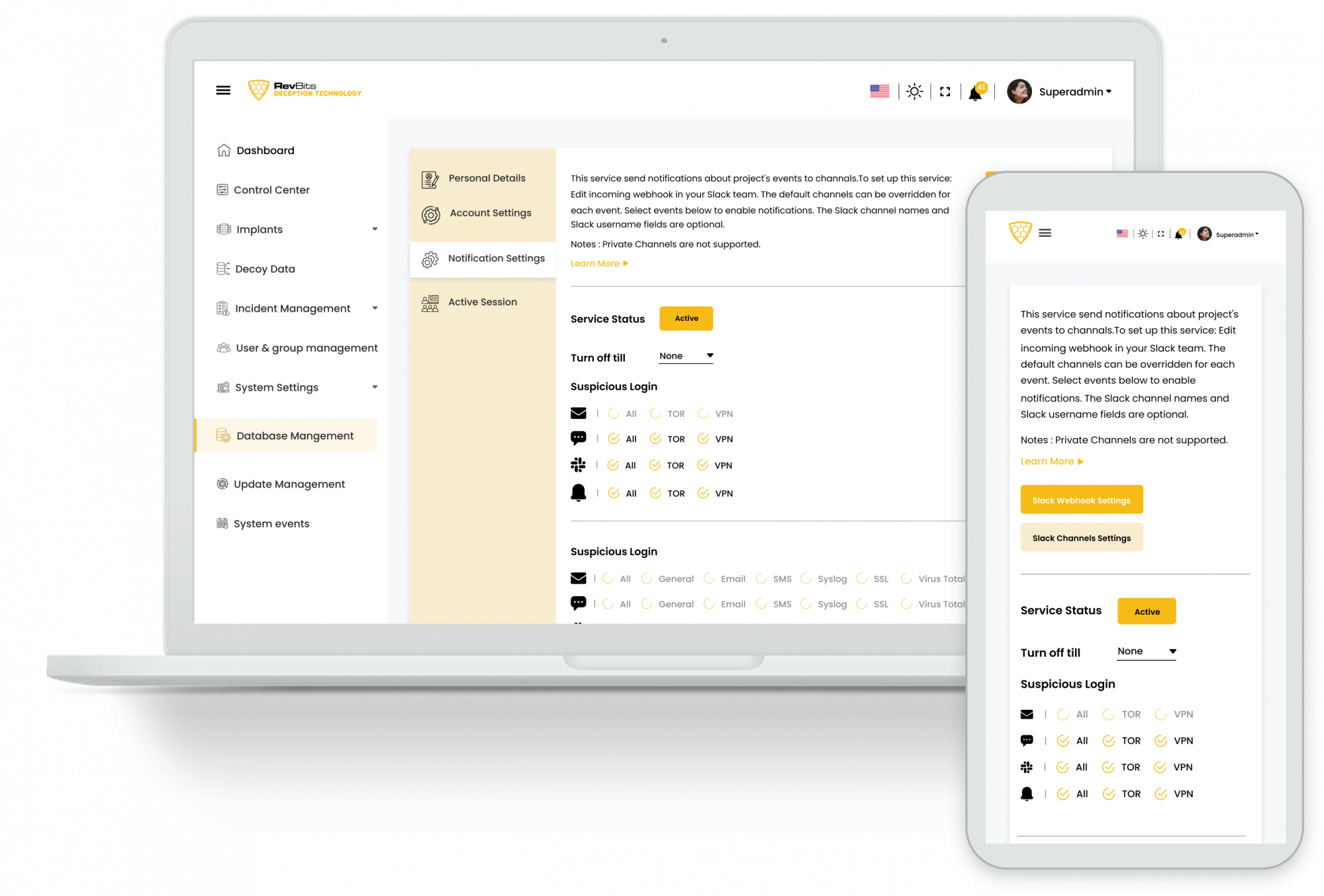
Advanced Reporting and Integration – RevBits deception technology integrates with SIEM products to deliver real-time alerts. SMS and email alerts are sent to system administrators about incidents. Detect and block attacks designed to impersonate trusted senders. Non-malware attacks are thwarted by real-time analysis of emails, detection of header anomalies, lookalike domains, and sender spoofing.
Additional Features
Manage Malicious Actors and Insider Threats – RevBits deception technology is designed to address the malicious actor who has gained unauthorized access on the network, as well as the insider threat that compromises the network to access valuable assets. In both cases, the goal is to lure the threat with real servers and, once there, trap the threat and prevent it from escaping. RevBits deception technology is designed to meet these two vital requirements in deception technology.
Easy to Deploy, Easy to Manage – Powered by RevBits, trap real database servers (MySQL, PostgreSQL, MSSQL, etc.), file servers (FTP, SMB, etc.), network devices ( routers, firewalls, etc.) and all common network protocols (SSH, RDP, VNC, etc.) can be launched with a single click. A central dashboard allows network administrators to manage, configure and monitor all honeypots throughout their enterprise.
Unique Design – RevBits deception technology's dual-layer virtualization architecture provides superior encapsulation of attackers in honeypots. In addition to security benefits, RevBits' deception technology allows for easy deployment, efficient management, and low resource consumption.
Benefits
Affordable Deployment – Through a unique design, RevBits deception technology enables extensive decoy deployment without increasing resource usage. A RevBits server can host multiple honeypots on the network.
Increase the value of deployment through successful threat hunting – The value of deploying RevBits deception technology is increased due to the use of real server-based traps. Using real server-based honeypots increases the likelihood of capturing the malicious actor and preventing them from accessing other important assets on the network.
Built with security in mind – RevBits deception technology uses two-layer virtualization to ensure the capture of the malicious actor or insider threat. This dual-layer virtualization ensures that the investment in the product is profitable: once trapped in a decoy of RevBits deception technology, the likelihood that the malicious actor will be able to escape is significantly reduced.
Simple Deployment – RevBits deception technology is easy to deploy: no specialized software required for deployment, multiple images ready to use in the cloud.
Requirements