Endpoint Security
As an intuitive, high-performance security software, RevBits Endpoint Security blocks the most sophisticated attacks. RevBits Endpoint Security is the only solution available that performs a three-phase threat analysis.
Analysis and Detection
Three-phase scanning of new executables - New executables are isolated and scanned before release to protect the network. The analysis is first performed with comparisons of firms; second with machine learning verification and third by behavioral analysis.
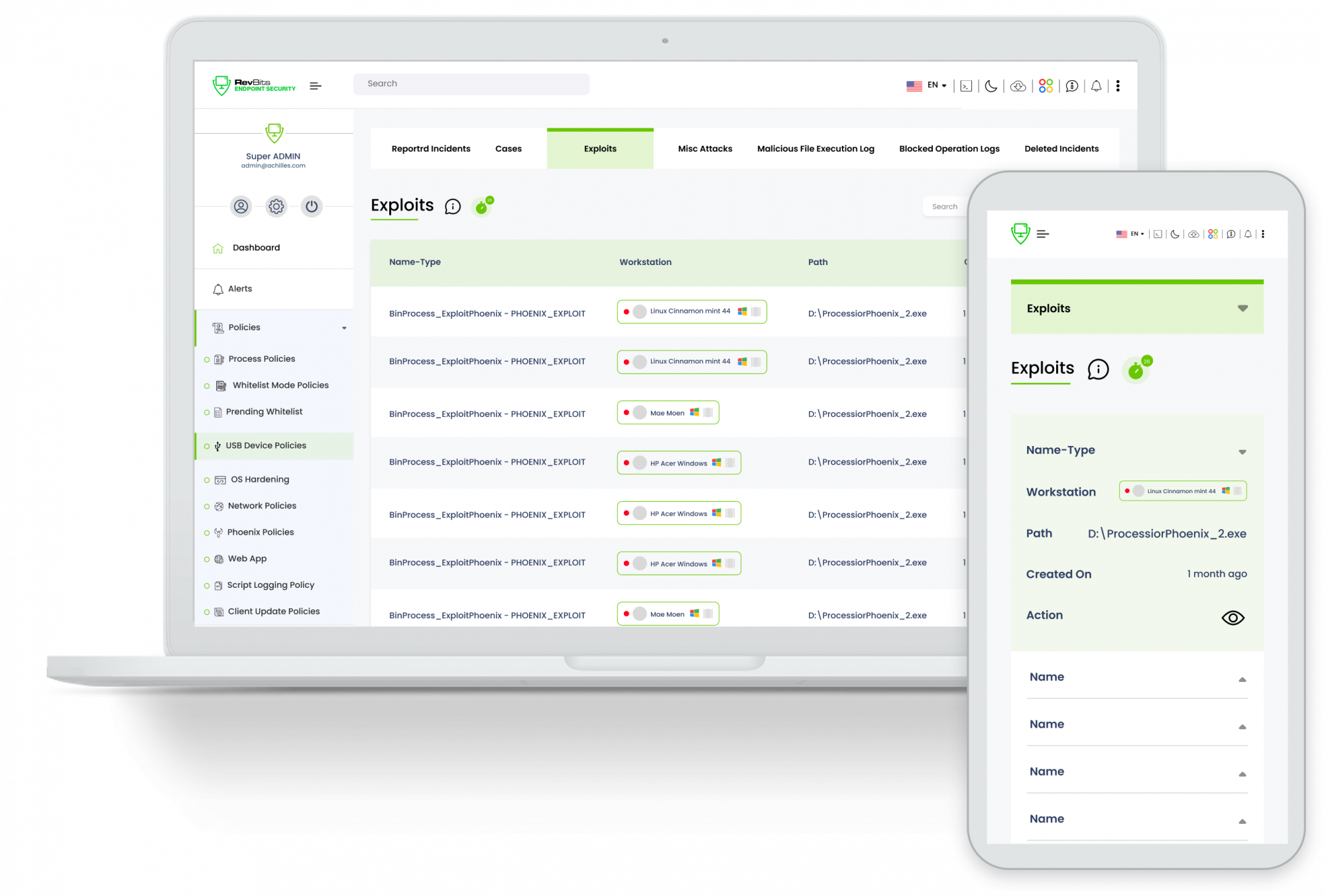
Advanced Exploit Detection – RevBits Endpoint Security's vulnerability detection targets vulnerable applications and processes, including but not limited to web browsers, desktop publishing software (such as Microsoft Office or Adobe Reader), and others.
Process Recording – RevBits Endpoint Security records all process termination and execution information, including its hashes (MD5, SHA 1, and SHA2), workstation, username, and timestamp for six months.
Effective anti-ransomware module – Through its sophisticated file system sandboxing feature, RevBits Endpoint Security can detect and block all types of simple and sophisticated ransomware.
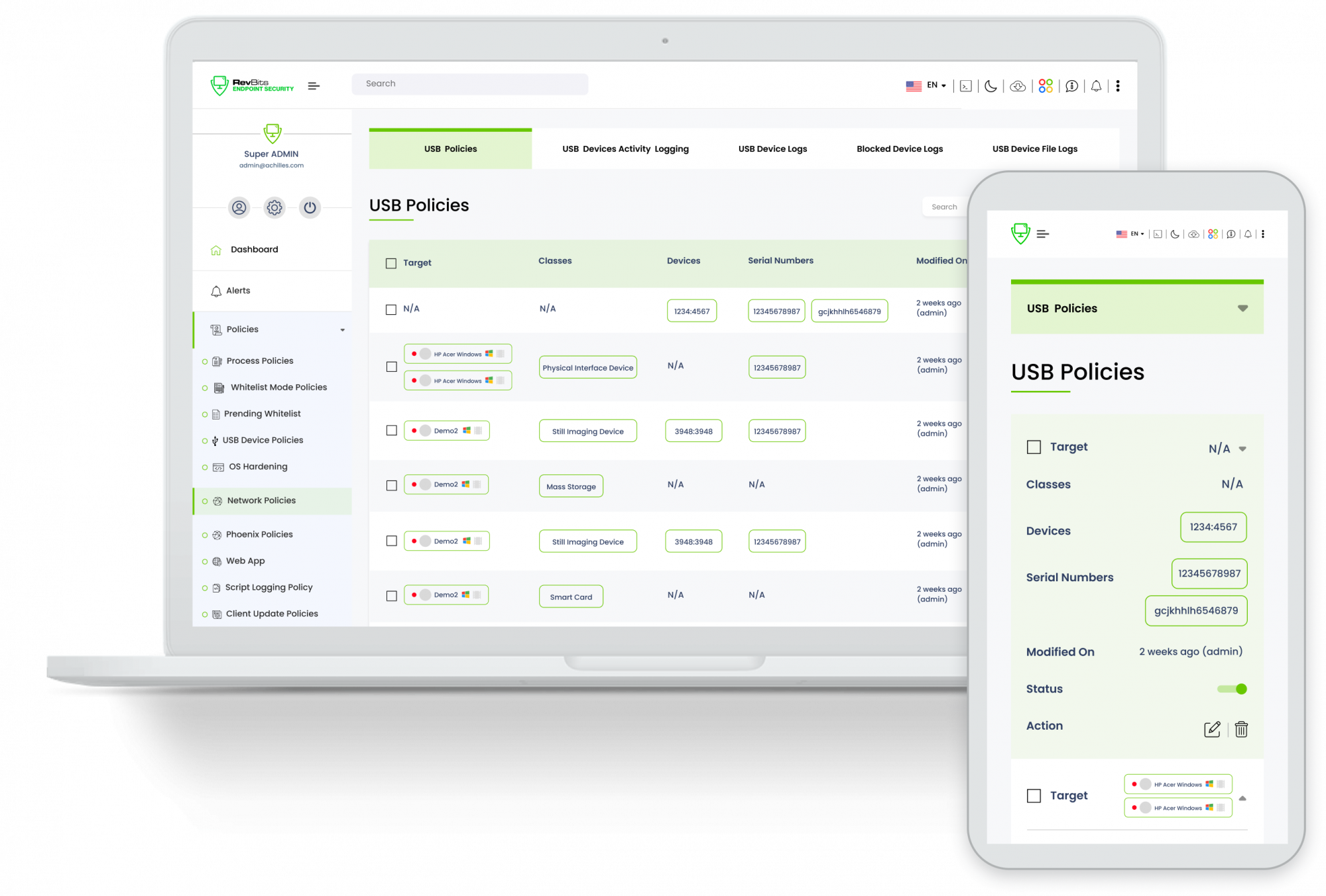
Control USB devices - Administrators can access a comprehensive whitelist/blacklist structure that provides four device description applications; Vendor ID, Product ID, Serial Number, and Device Type. Additionally, specific ports can be enabled or disabled on workstations.
Host-Based Firewall - System administrators can adjust network and firewall rules for both individual workstations and groups of workstations.
Immediate Host Isolation – Protect the network automatically or manually by confining potentially infected hosts.
Automatic Forensic Evidence Extraction – Automatic pre-shutdown or on-demand forensic evidence extraction to assist in rapid incident response.
Advanced Notification System – RevBits Endpoint Security integrates seamlessly with all SIEM solutions. Additionally, administrators will be notified by SMS and email when an incident occurs.

Endpoint Investigation
Truly innovative - Two US patents for a unique technological breakthrough to detect and block kernel access from signed and unsigned drivers.
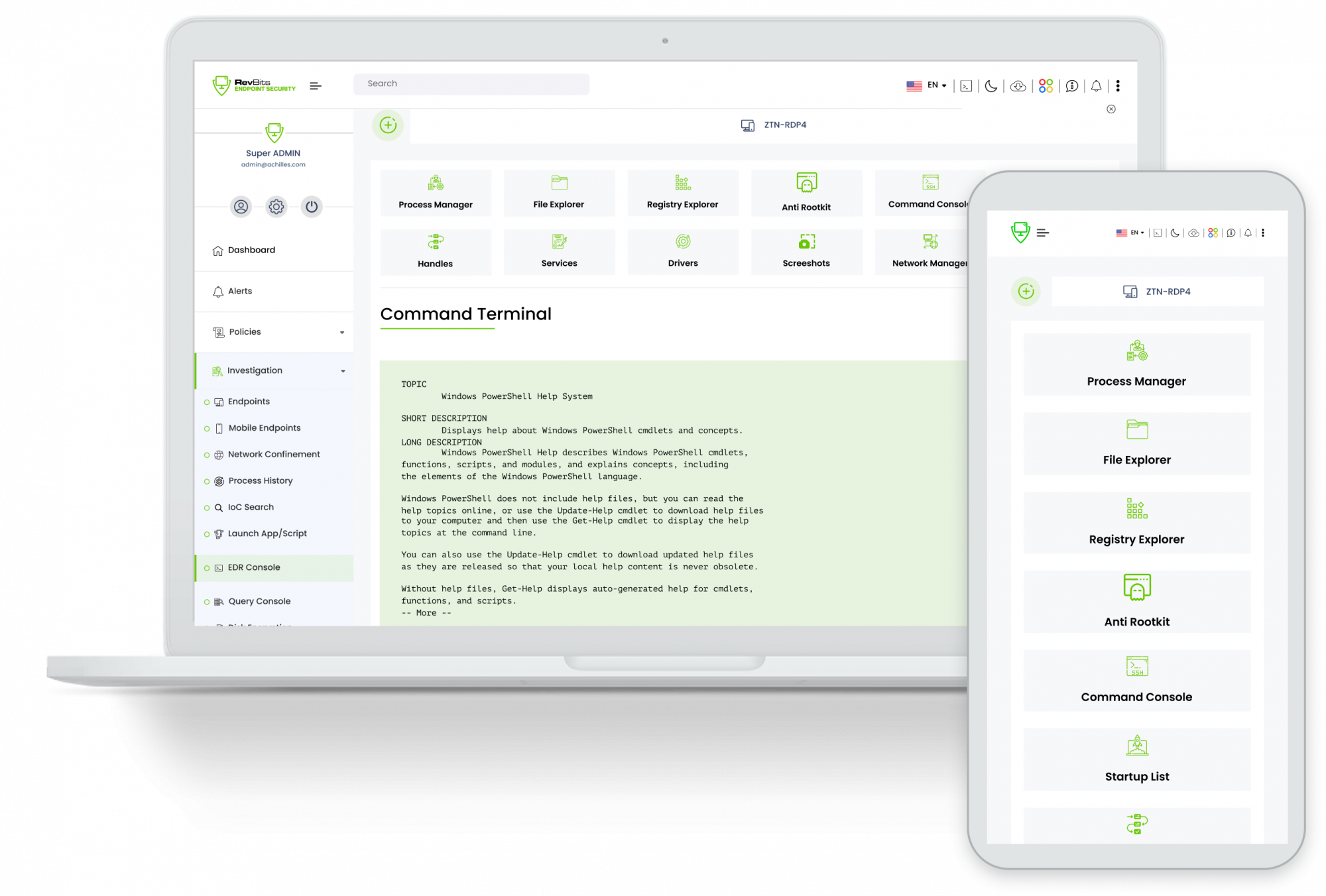
Command Line Capability – Powershell and command line prompt terminal to interact with all remote Endpoints.
Full EDR Menu - Interact with remote endpoints to include: Process, File Explorer, Registry Explorer, Command Console, Services, Drivers, Anti-root Kit, Startup and Tools.
GUI control over all endpoints - Graphical interface for all remote endpoint EDR operations.
Deep Endpoint Control – Interact with remote endpoints to control registry explorer, file explorer, process explorer with process tree hierarchy.
Full Remote Control – System administrators can remotely dump process memory, raw disk, and raw drive dump.
Benefits
Reduce the chance of a successful malicious execution – RevBits Endpoint Security protects against all types of Endpoint threats on any type of network through its unique three-phase scan of new executables. From the least sophisticated to the most sophisticated malware, RevBits Endpoint Security is designed to detect and block their execution and save your network from a costly breach.
Stop malware before it runs – By isolating and thoroughly analyzing new executables, the chance of a successful attack is greatly reduced.
Comprehensive forensic analysis – By collecting highly useful information about executions, scripts and commands, system administrators' time and expenses for classification and cleanup are greatly reduced. This capability extends functionality to meet compliance needs and standards.
Reduce the need to hire external forensic and remediation companies – RevBits Endpoint Security's EDR module allows system administrators to conduct internal network investigations, minimizing the need to use external resources.
Reduce the success of the insider threat – The cost to the organization of an insider threat is substantial. The costs associated with breaches and data theft can be mitigated and controlled through the extensive USB policy management capabilities of the RevBits Endpoint Security agreement.
Additional Features
Fully featured in an Air-Gap environment – RevBits Endpoint Security can be fully deployed in an Air-Gap environment. All product features are functional and actionable without an Internet connection.
Detect and contain malware at the endpoint – RevBits Endpoint Security performs a unique three-phase scan on all new executables. This analysis includes signature scanning, machine learning, and behavioral analysis, maximizing the accuracy of malware detection and minimizing false positives.
Complete visibility and control with RevBits EDR – Complete, low-level details of processes, threads, registry, file system and kernel are visible and controllable through the RevBits EDR GUI, not a simple command line. System administrators can run commands in PowerShell or Command Prompt on workstations. One-click forensic evidence extraction, memory imaging, and disk imaging capabilities make RevBits EDR the most sophisticated EDR solution on the market.
Intuitive dashboard reveals actionable insights – RevBits Endpoint Security provides an easy-to-understand, real-time view of threats through its modern web interface. The dashboard presents extensive historical information for all executables in a clear, simple tile and maintains detailed process information for six months.
Detailed historical information of all commands executed – RevBits Endpoint Security logs and reports all commands and scripts executed in all command and script interpreters, including Windows Command Prompt, Powershell, VBScript and JScript.